Worldwide spending on cybersecurity is expected to reach USD 133.7 billion by 2022. Given the losses associated with a cyberattack average nearly $4 million, companies can not afford to ignore the security risks associated with cybercrime.
We’ll discuss the main types of attacks then discuss the cybersecurity tips to minimize the security risks to your company and clients.
Types of Cyberattacks
There are 8 main types of cybercrimes used to disrupt businesses for financial gains or steal trade secrets. They consist of:
- Malware attack
- DoS and DDoS
- MitM
- Phishing and spear-phishing attacks
- Drive-by attack
- Password attack
- SQL injection attack
- XSS
Let’s explore each of these types of cybersecurity attacks so you can understand how they work.
What is a Malware Attack?
Malware attacks are performed by tricking a person into unintentionally downloading unnoticeable software to the user but allow the hacker to steal the personal or company information. These can be added by clicking on a link or visiting a website with malicious code.
What are Denial-of-Service (DoS) and Distributed-Denial-of-Service(DDoS)?
DoS and DDoS attacks are typically used on major entities such as publicly traded companies and governments. They work by tying up the server by sending requests from fake IP addresses that never respond to the server, tying up the resource in the process.
The difference between a DoS and DDoS is the number of devices being used to tie up resources. A DoS involves one machine attacking the server. In contrast, a DDoS can involve hundreds or thousands of devices being used by one person or a collective of people to overwhelm the servers.
What is a Man-in-the-Middle Attack (MitM)?
MitM attacks are often carried out on public Wi-Fi networks, to which anybody has access. A hacker will exploit the ability for anyone to access the network by using special code to scan the router for vulnerabilities and make it where the user has to pass through the hacker’s system on the way to the sites they are going to. This gives the hacker access to passwords and credit card information. A variation of this called Man-in-the-Browser attacks allows cybercriminals to do the same thing without being in the same location as the computer, making it easier to collect the data.
What are Phishing and Spear-phishing attacks?
Phishing attacks are email attacks that appear to be from a trusted source, like Amazon or Australian Post, but when you click on the link, it takes you to a malicious site that logs your email and password so the hackers can steal it. These emails are sent to many people in the hopes that a few would fall for them. However, since 51% of people use the same password for all their accounts, a single employee falling for a phishing scheme can give hackers access to company resources even if their personal accounts were hacked.

A spear-phishing attack is similar but is targeting a specific person. The hacker uses social media and the internet to research an individual they wish to target and poses as someone they trust. Because this strategy is more targeted, people are more likely to fall for it2.
What is a Drive-by attack?
A drive-by attack does not require clicking on anything. These can be added to normal sites that have security gaps or even advertisements on sites like Facebook. Then, just by scrolling past it, code will be triggered that analyzes your device for weaknesses and adds malicious code to download malware on the user’s device or send information back to the code’s creator.
What is a Brute-force attack?
These are attacks strictly focused on finding the password and accessing it. Some devices will test 100 Billion username/password combinations per second. If allowed to persist continually, they will eventually find one that works. Because many people use important words in their passwords, this can be done with a dictionary attack limiting the possibilities dramatically by only using real words1.

What is an SQL injection attack?
SQL injections are attacks that target databases that are poorly constructed. They do this by inserting instructions for an SQL query into the user inputted information in an attempt to access the database and access, alter, or delete it for purposes of espionage or profit. They tend to be most successful in older ASP or PHP assets, while SQL injection is more difficult to achieve in J2EE and ASP.NET resources. OWASP.org has some useful information on SQL injection attacks and how to deal with them.
What is a Cross-site scripting (XSS) attack?

Cross-site scripting is similar to an SQL injection attack but focuses more on sites that allow users to comment without being filtered to ensure no corrupt code in their responses. Once the code is on the site, it will run in a users browser. Because JavaScript is the most commonly used, this tends to be the code they target, but VBScript, ActiveX, Flash, and CSS are also potential targets for cross-site scripting attacks.
Now that we’ve discussed the most common attacks let’s look at what can be done to protect your company, employees, and customers from these attacks.
Tips for Protecting against Cyber Attacks
There are numerous approaches you can take to protect your organisation against cybersecurity risks. Most involve using technology, but another crucial part is training. We’ll discuss:
- Keeping Software Updated.
- Encryption
- Email Security Software
- Firewall’s
- VPNs
- Multifactor Authentication.
- Identity Providers
- Backing up Data
- Password Best Practices
- Document Policies.
- Importance of Training.
- Cyber Security Insurance
Keeping Software Updated
According to Cyber Observer, 80% of cyber attacks could be prevented through basic actions. The easiest and most basic way to protect your technology assets is to keep software updated. By updating your software, you are removing known security threats from the software, making it harder for malicious actors to take advantage of known vulnerabilities.
Many companies that provide SaaS have the ability to update automatically. However, if some of your tech stacks does not, I suggest having a specific day of the week/month to update them. Patch Tuesday is when Microsoft, Oracle, and other software companies release patches for their software. It coincides with 11am-12pm on the second Wednesday in Brisbane. They also sometimes release patches on the 4th Tuesday at the same time. This is a perfect time to make sure all your software is updated. Check out our source code upgrades page to learn about the services we offer for updating software.
Encryption
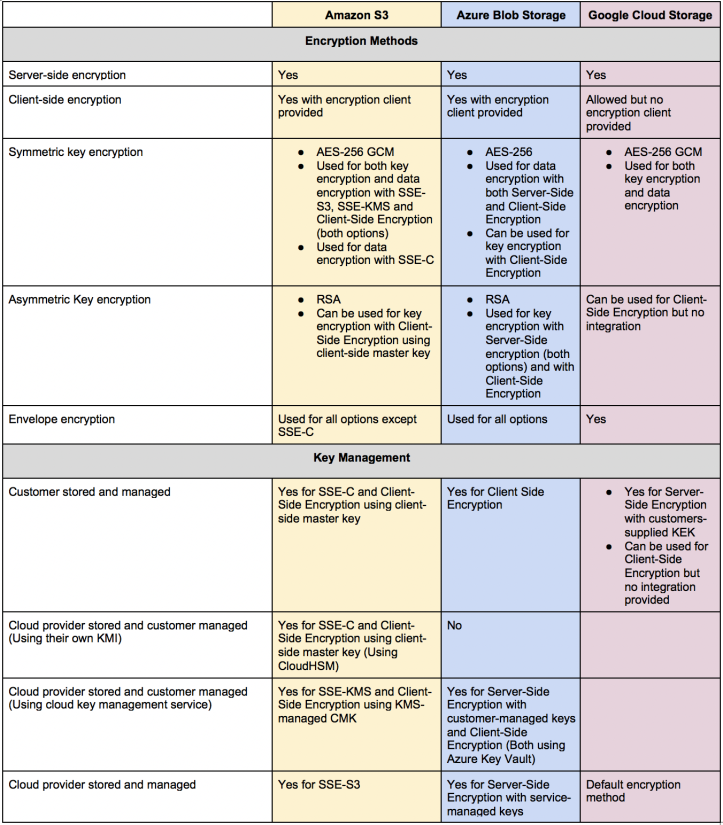
Encryption is used to make it harder for an unauthorized user to access and understand data. It has been used as far back as 1900 BC by ancient Egyptians using a cypher to translate it. Today the techniques are much more complicated but follow the same principles.
There are two basic types of encryption, at rest and in motion. Rest protects the data stored in the database; while encryption is in motion for a while, the data is transmitted. Amazon, Azure, and GCP all offer both encryptions at rest and in motion. Furthermore, they offer similar encryption offerings in motion but have some meaningful differences in the encryption at rest.
The major differences between the three providers come down to:
- Ease of use
- configurative
- Integration
- Documentation
Azure and GCP have more centrally located configurations because Amazon was the first mover. Still, Amazon has more options, better documentation, and more people who are experienced in working with it. GCP allows most of what the others do but requires a custom integration (which we can do). Azure tends to balance ease of use, configurative, integration, and documentation, so we recommend it over the other two.
If you want more technical reading about the three cloud providers encryption, check out Cloud Architect Musings blog about them.
Email Security Software
Email security software will perform functions such as scanning emails for malicious files and links, email archiving, continuity in server failure, and more.
The major benefit here is scanning emails for malicious files and links. This feature helps prevent employees from clicking on phishing emails and helps keep your network secure. Some email providers, such as Gmail, include similar features by default. Have your admin check the settings to see if the settings in your email provider are enough for your organization.
Firewalls

Firewalls are used to block certain people and IP addresses from accessing the server. They can be hardware or software. You block all access except certain IP addresses and close off any unused ports to protect the server. This lets you control who enters the server and is properly protected so that unapproved people have a more difficult time.
VPNs

Virtual Private Networks are basically encrypted private channels to enter into the office. They are basically an extension of encryption where the user has to be approved before they enter, and the entrance is encrypted. These are standard in business today and will be even more so with the growth of remote workforces. Make sure you are using secure software.
Multifactor Authentication(MFA)
Multifactor Authentication requires confirming your identity with a code from multiple devices: typically, it will be your phone, an app such as Google Authenticator, and an email. These are time-based, so you have to have direct access to them to meet all the steps.

MFA reduces the likelihood of unauthorized participants getting access to your account even if they have the password. This started in the banking industry but has become commonplace in most industries. It greatly reduces the impacts from many attacks by making it where their attempt to access the system is denied due to the lack of code from the app or phone. Make sure you are using them whenever possible.
Identity Providers

Identity providers are trusted companies like Google and Facebook that provide proof of identity without protecting the site information. It’s good for companies as it reduces the data they have to protect and consumers’ risks in data breaches. I discuss Identity providers more in our blog about the Identity Providers FAQ.
Backing up Data

Backing up data is essential for ransomware. When someone tries to lock you out of your server using ransomware, a recent backup will allow you to get back up almost instantaneously. Without it, you’ll have to pay them or lose your data. It’s easier than ever to do this. Make sure you have recent backups.
Password Best Practices
Using password best practices is essential for protecting your company’s assets. Having longer passwords, randomly generated passwords, and special characters included in the password are some of the easiest ways to make it harder for people to access your accounts. In addition, combining these with MFA and identity providers makes it a much more challenging task for unwelcome parties to get access to information.
Document Policies.
All of these best practices should be documented where it is easy for everyone to review them. They should also be monitored or audited to make sure compliance is being achieved.

Importance of Training.

Training your people to follow these practices is the final key to the puzzle. Without proper training, best practices will only be partially effective. Human error is still the number one cause of data breaches. Make sure to train, audit, and include in performance reviews whether people are following security procedures.
Cyber Security Insurance
Despite doing everything right, there’s still a chance your data will be compromised. However, with an average cost of $4 million lost during a data breach, cybersecurity insurance is worth the investment to protect the business from financial losses from data theft.
We covered the types of security risks businesses face and the ways to mitigate the risks from cybercrime. I hope this has helped increase your understanding of cybersecurity. If you need help implementing or improving these cybersecurity best practices, reach out to team@flyingdonkey.com.au, and we’ll help you get up and running.





